
Why Flight Searches Take Longer Than Searching the Entire Internet
When you look up a flight online, it can feel surprisingly slow. You enter your departure date, your destination, and maybe a preferred time and then you sit and wait. Meanwhile, you know that Google can search through hundreds of billions of webpages and show results in a fraction of a second.
So why does finding a seat on a single flight take longer than searching the entire internet?
To understand this, it helps to look at how airline search systems work behind the scenes and why their process is nothing like a normal web search.
The Scale of Airline Flight Data
Let’s start with the size of the data involved.
Take American Airlines as an example:
- Average daily flights: about 3,582
- Destinations served: around 120
- Flight combinations: tens of thousands when you factor in connections, fare classes, seat types, loyalty programs, and fare rules.
On paper, this doesn’t seem overwhelming. A few thousand flight records should be easy for modern computers to process especially compared to Google’s massive global index.
But airline searches involve far more than just looking up schedules.
Airlines Aren’t Just Searching They’re Calculating
When you click “search,” the airline isn’t simply trying to find flights that match your date and destination. Airlines run your request through complex systems designed to answer a very different question:
What is the highest price this traveler is likely willing to pay?
To do this, airlines use revenue-management engines high-powered algorithms built to predict human behavior and maximize profit. These systems evaluate things like:
- Your past travel purchases
- Your device and browsing behavior
- How often you check the same trip
- Your digital habits and online footprints
- Market demand for the same route
- Local events or holidays that might increase urgency
- Travel patterns of people in your demographic or social circle
All of this happens behind the scenes in seconds. The system isn’t just finding flights—it’s ranking and pricing them based on how the airline expects you to behave.
This level of analysis requires enormous computing power and decision making rules. That’s why the search process can feel slow: the system is doing complex, real-time pricing calculations, not just simple lookups.
Why Google Is Still Faster
Google’s search works differently. Instead of calculating a custom price for each user, Google retrieves information from an index it has already built. Think of it as pulling books off a shelf that’s already organized.
Airlines, on the other hand, must calculate the “value” of each seat at the exact moment you search.
In short:
- Google: looks up information from a pre-organized index.
- Airlines: run real-time pricing models based on your behavior and the behavior of millions of travelers.
It’s the difference between asking a librarian for a book versus asking an accountant to evaluate the value of every book in the library before handing one to you.
Dynamic Pricing: The Real Reason Behind the Delay
The biggest culprit is dynamic pricing, a strategy airlines use to adjust prices constantly based on supply, demand, and consumer behavior.
This system tries to answer questions like:
- Is this traveler price-sensitive or in a rush?
- Is there a holiday or event affecting demand?
- Have similar travelers paid more for this route?
- Should the fare be raised or lowered in the next few minutes?
The result: every search is unique. Two people searching for the same route at the same moment may see different pricing.
What This Means for You
For everyday travelers, this explains why searching for flights can feel slower and more unpredictable than searching the web. It isn’t your device. It isn’t the airline website struggling.
It’s the pricing engine working to determine:
- What flights fit your needs, and
- What price you’re likely to accept
Small-business owners can see the broader lesson here: companies that rely on dynamic pricing or predictive analytics naturally require more complex systems especially when they’re adjusting prices in real time.
Final Thoughts
Even though flight searches deal with fewer records than a typical internet search, they are far more computationally complex. Airlines aren’t just showing available flights; they’re performing real-time financial calculations based on countless factors related to you and the market.
So the next time that loading wheel spins while you search for a flight, remember: it’s not slow because it’s simple it’s slow because the system is working very hard to predict what you’re willing to pay.

 ️ Assumptions for Model Accuracy
️ Assumptions for Model Accuracy Define the Core Equation
Define the Core Equation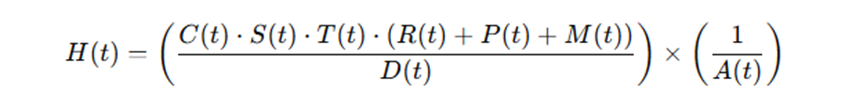
 Apply for t = 5 (Year 2028)
Apply for t = 5 (Year 2028)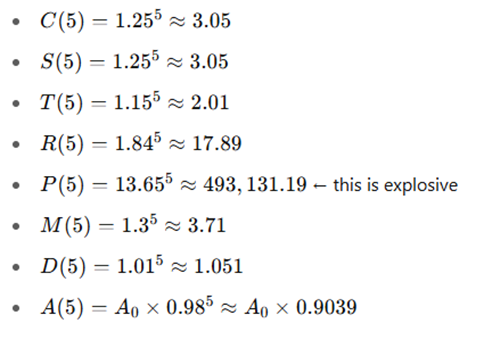
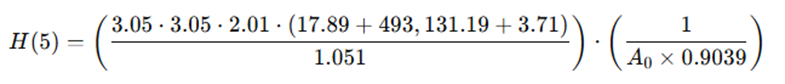
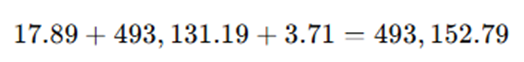
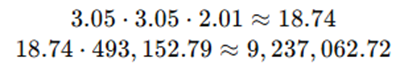
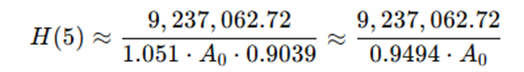
 Interpreting the Result
Interpreting the Result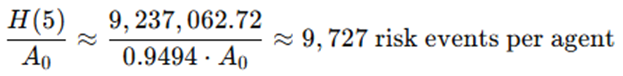
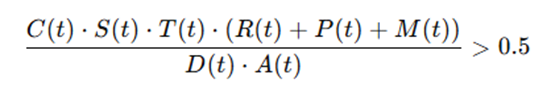
 Takeaway for Real Estate Brokers
Takeaway for Real Estate Brokers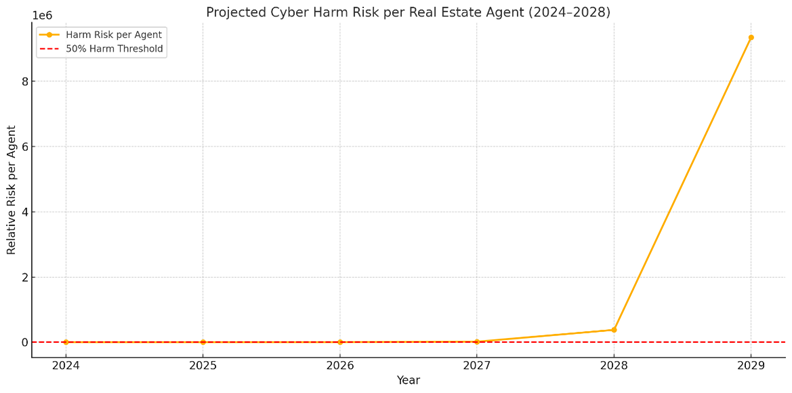
 Case Studies in Controversial Apple Business Practices
Case Studies in Controversial Apple Business Practices The 6 Pillars of a Secure Password Manager
The 6 Pillars of a Secure Password Manager Proprietary (not open source)
Proprietary (not open source) ️ Control Over Data
️ Control Over Data Active Development
Active Development Bug Bounty Program
Bug Bounty Program ️ Well Established
️ Well Established Large Community
Large Community 2FA Support
2FA Support Platform Support
Platform Support Browser Extensions
Browser Extensions Pricing
Pricing